Cyber-physical Security Training Program 2023 Curriculum
Expected Learning Outcomes of Programs
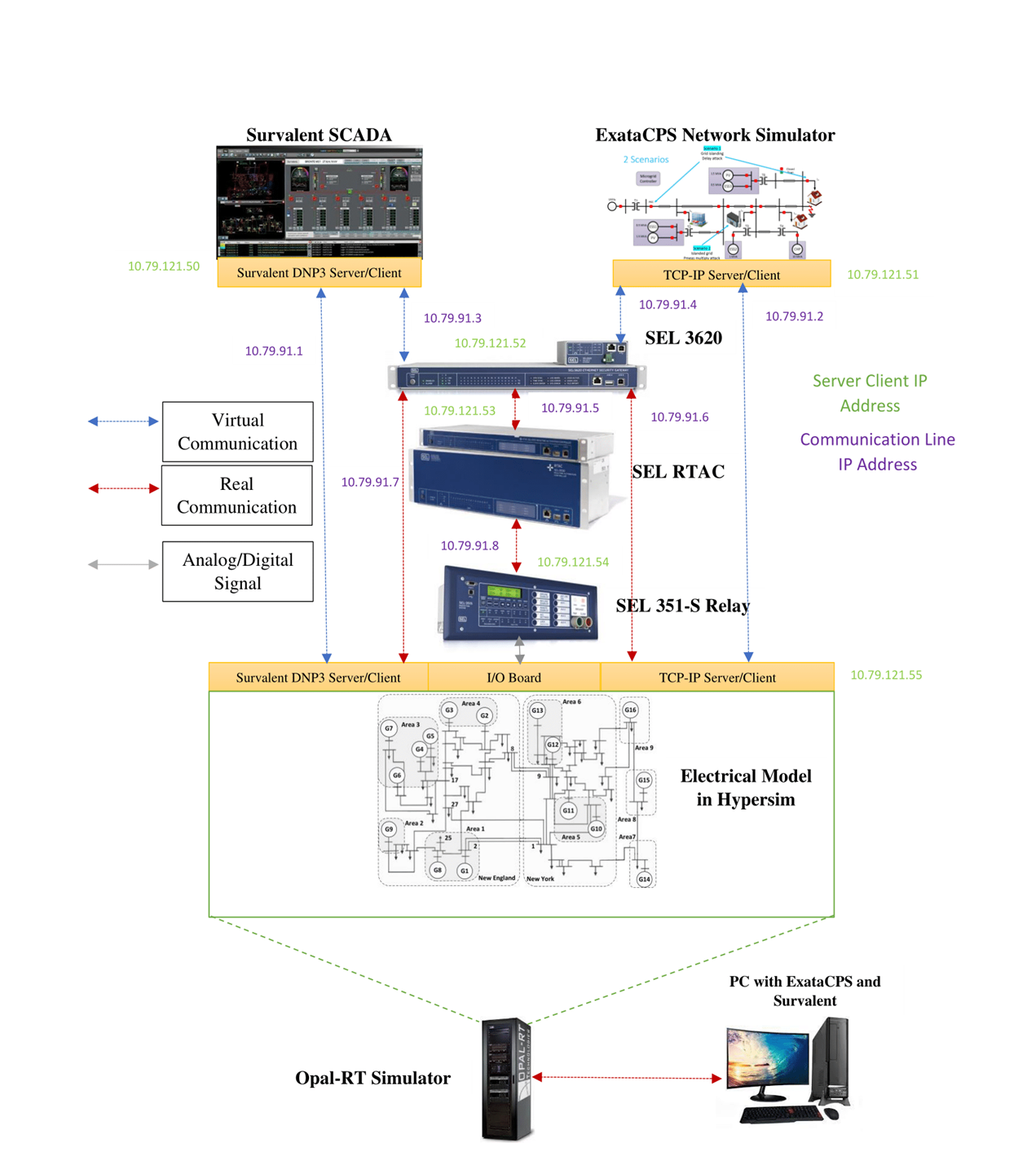
Module 1: Electric Utilities Cyber-Physical Operations and Security
- Fundamentals of electrical grid and wind energy operations.
- Understand cyber-physical process in electric utilities and wind operations.
- Hands-on lab learning experiences with Supervisory Control and Data Acquisition (SCADA), electrical grid attack surfaces, methods, and tools.
- Cyber-physical security training using the real-time simulator testbed.
Module 2: Computer Networking and Security
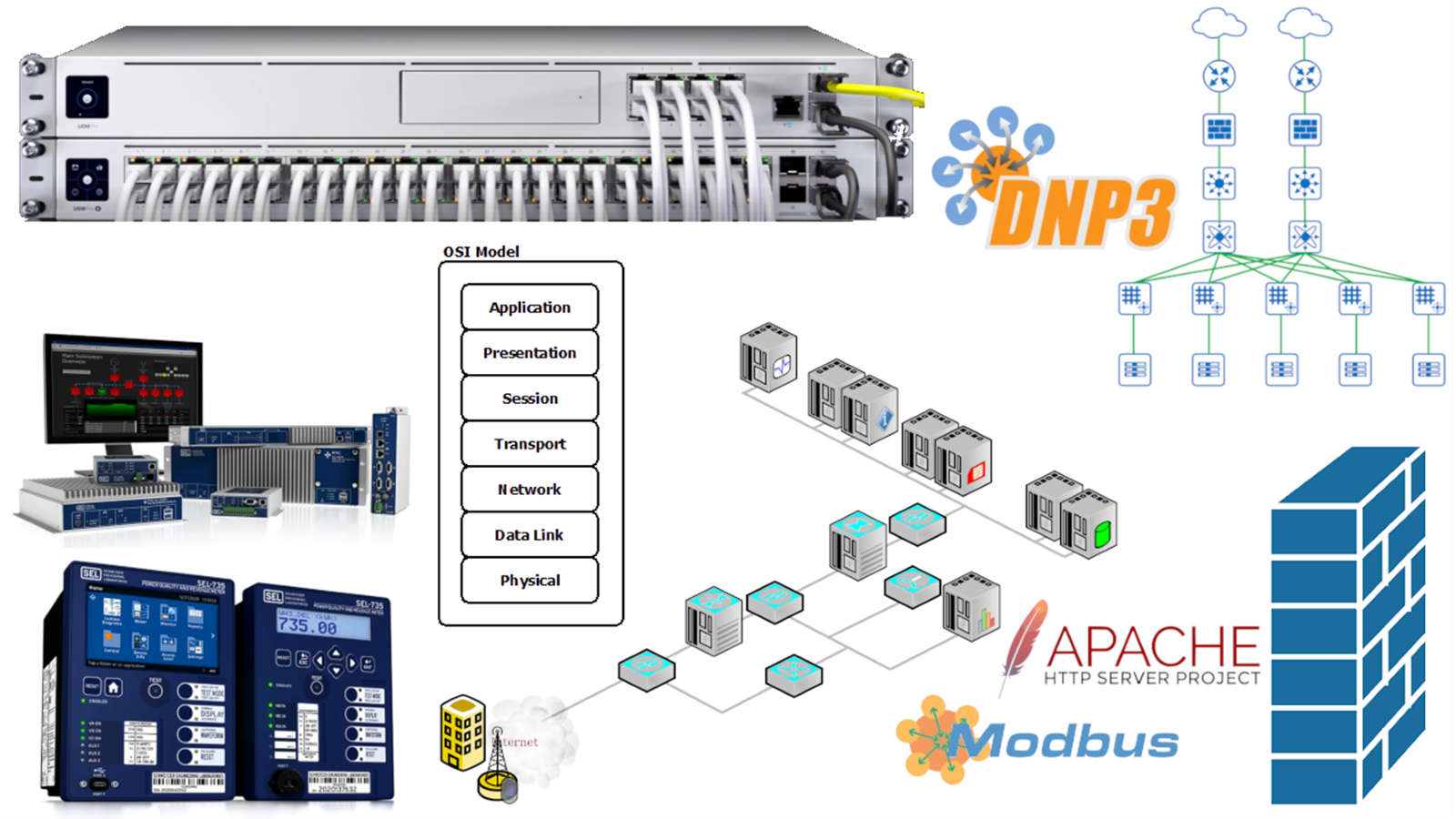
- Understand computer networking and relevant networking devices and infrastructures.
- Understand networking protocols, routing, TCP/IP tools and commands, and ARP.
- Understand cybersecurity attacks, including man-in-the-middle attacks, DOS attacks, etc.
- Cyber risk assessment and management with an emphasis on application to ICS analysis.
- Hands-on experimentation on the setup of a basic network, routing, DNS, HTTP, and DHCP servers.
- Hacking demonstration and mitigation in the experimental network.
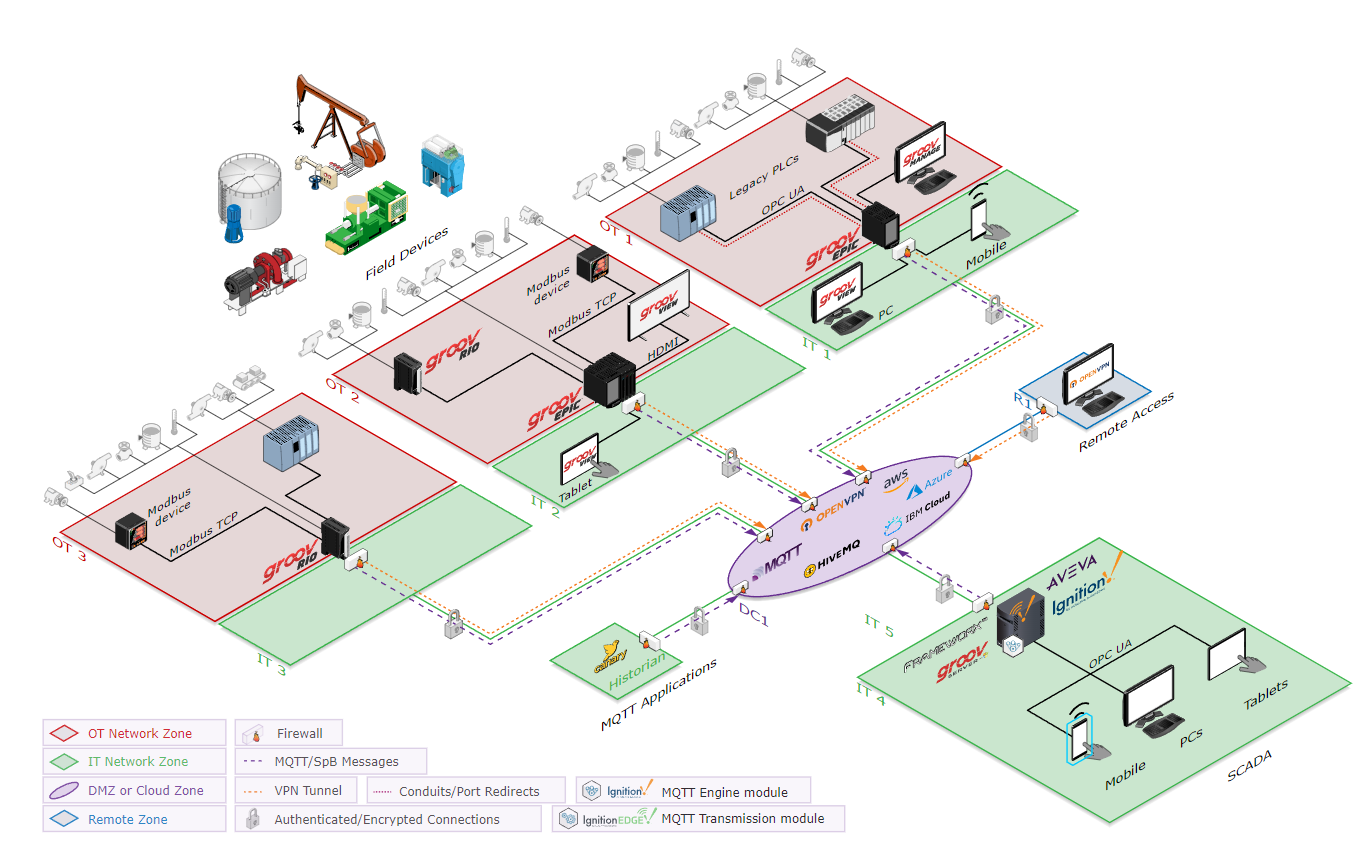
Module 3: Cyber-Physical Systems (CPS) for industry and microgrid environment
• Understand the fundamental concept of CPS to the industrial environment.
• Understand basic cybersecurity structures and standards.
• Hands-on experience in penetration testing of cybersecurity structures.
• Hands-on experience in control and monitoring of microgrid.
• Hands-on experience on Epic Groov for CPS.
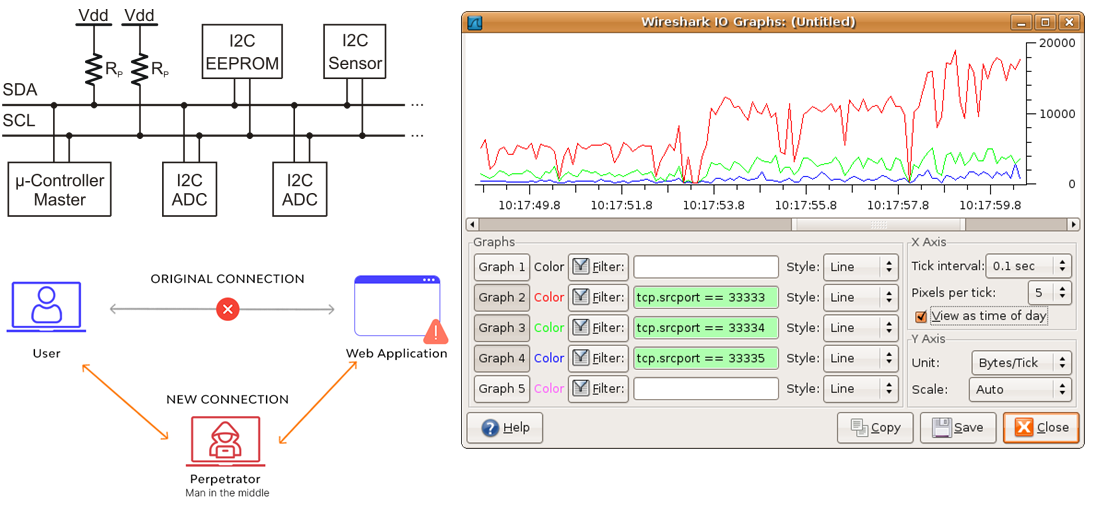
Module 4: Cyber-physical security – Encrypted Communication Channels, I2C protocol, and SCADA systems
- Study the I2C protocol and its vulnerabilities and utilize a device to hack into I2C communication between devices.
- Understand man-in-the-middle attack study and how it could affect SCADA systems.
- Use unknown/untrusted Universal Serial Busses (USBs) and study the importance of ensuring they are free of malware.
- Examine how Wireshark can be used to watch wired and wireless internet traffic and what encrypted and unencrypted data looks like.
- Learn how to use log files to study cyber events.
- Learn about cyber attack events and get an idea of what vulnerabilities SCADA systems have.
National Wind Institute
-
Address
1009 Canton Ave., MS 3155 Lubbock, TX 79409-3155 -
Phone
National Wind Institute - 806.742.3476; Renewable Energy - 806.742.6284 -
Email
National Wind Institute - nwi@ttu.edu; Renewable Energy - windenergy@ttu.edu
